Critical Vulnerability Fixes Available For Juniper Devices

Juniper has addressed multiple critical vulnerabilities in Junos, Junos Space, and JATP devices. Administrators are advised to update to the latest OS version on any affected Juniper device.
背景
Juniper has released a number of security advisories this week which include critical vulnerabilities across many of its devices. The Juniper Advanced Threat Prevention Appliance (JATP) update removes hardcoded admin credentials, while the Junos updates include patches for remote code execution (RCE) and denial of service (DoS) vulnerabilities. Junos Space network management devices are also vulnerable to a memory allocation vulnerability which could lead to DoS and RCE attacks as well.
分析
JSA10918 addresses 13 vulnerabilities, including CVE-2017-11610, CVE-2018-0020, and CVE-2019-0022 for Juniper’s ATP, a malware defense appliance designed to detect and prevent malicious activity on a network. An attacker could gain access to this device with hardcoded administrator credentials and disable a core defense against malware.

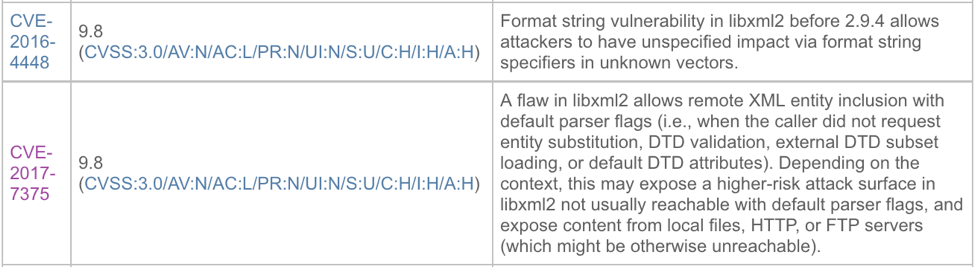
Among the many Junos updates, CVE-2017-7375 and CVE-2016-4448 addressed in JSA10916 could allow a remote unauthenticated attacker to send specially crafted extensible markup language (XML) packets that lead to privilege escalation or format string manipulation. Format string vulnerabilities allow attackers to execute commands when the device should be reading this user input as simple text.
JSA10917 for Junos Space addresses CVE-2018-1126, which relates to similar Junos vulnerabilities mentioned above. Attackers could take control of network management devices such as a Junos Space Appliance and redirect traffic to malicious sources, further infecting more vulnerable assets.

解决方案
Juniper recommends updating to the latest OS version of any of the affected devices or appliances you may have. Manual updates and appliance images can be found on Juniper’s download site here.
识别受影响的系统
A list of Nessus plugins to identify these vulnerabilities will appear here as they’re released.
获取更多信息
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
相关文章
- Threat Management
- Vulnerability Management







